Booz Allen's Experience by the Numbers

200+ experienced OT cybersecurity practitioners
15 of the 16 critical infrastructure sectors supported
40+ GICSP and GRID certification holders

300+ OT cybersecurity assessments conducted
8 of top 20 global pharmaceutical OT cybersecurity programs supported
100+ OT-focused threat detection analytics developed
Cyber Lab Environments
Production OT/ICS environments contain a variety of specialized equipment and software, while often facing strict engineering and change control processes. By mirroring these technologies in our labs, we're able to replicate real-world environments to test new products, validate vulnerabilities, demonstrate attacks, and test out security solutions—before we implement them.
Cutting-Edge Approach to OT and ICS Security

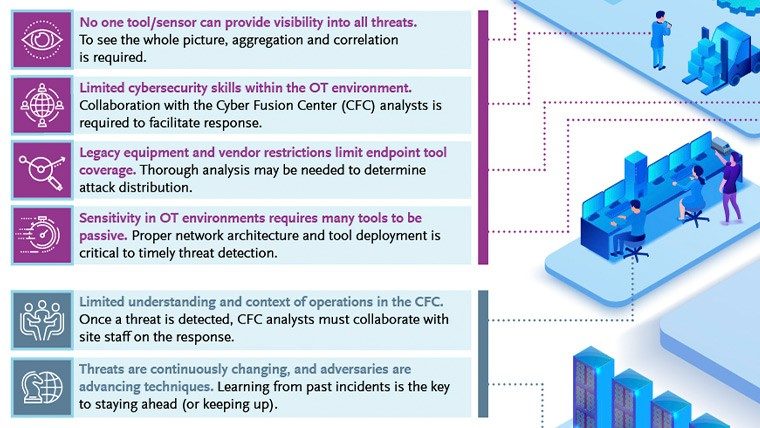
Adversaries are getting smarter and stealthier: They’re targeting OT/ICS like never before. At Booz Allen, we apply best practices and innovations developed across the federal and commercial space to solve complex challenges and stay one step ahead of threats.
Working with some of the world’s leading OT/ICS cybersecurity solutions providers, integrators, and OT vendors, we have developed cutting-edge solutions to secure your OT/ICS infrastructure. From integrating security into all stages of the system lifecycle to detecting and responding to advanced cyber threats, we build solutions to endure.
Find out more about our approach to OT/ICS security.
Our Work in Action
Meet the Experts
Related Content
Contact Us
Get more information about cybersecurity solutions or to speak with our experts.