When you're reverse engineering a new piece of malware in IDA (the Disassembler and Debugger developed by Hex Rays), you hope that IDA can identify the library functions in the sample, and you can focus on functionality unique to the malware itself.
Often that's not the case and IDA presents a list of functions named by default with “sub_” followed by the function’s address (Figure 1 – left). It’s much more helpful when IDA has the correct library function signatures and provides a list containing more descriptive names. (Figure 1 – right).

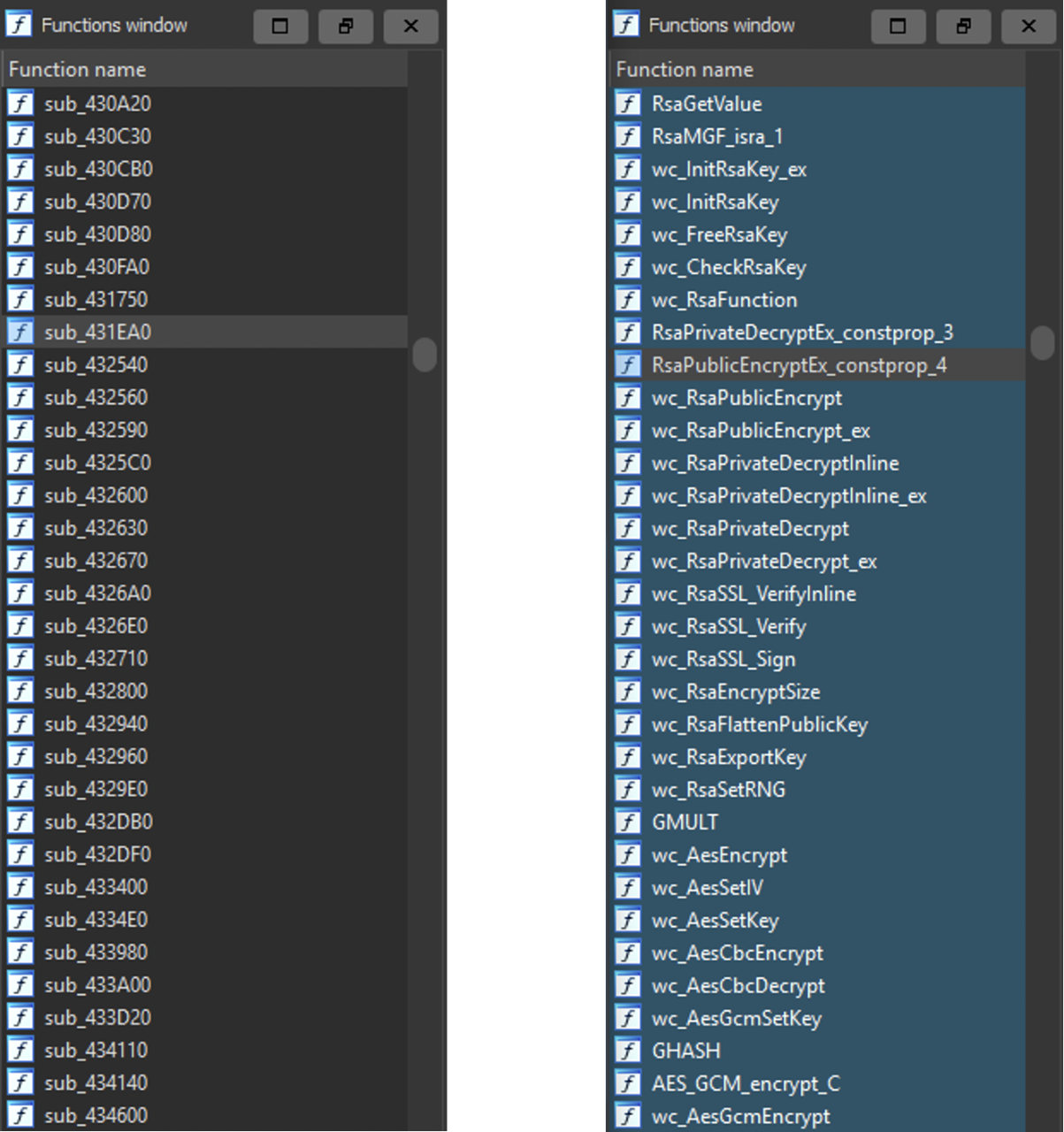 Figure 1 – Function list without (left) and with (right) signatures
Figure 1 – Function list without (left) and with (right) signatures
 Figure 2 – IDA graph overview of complicated function
Figure 2 – IDA graph overview of complicated function
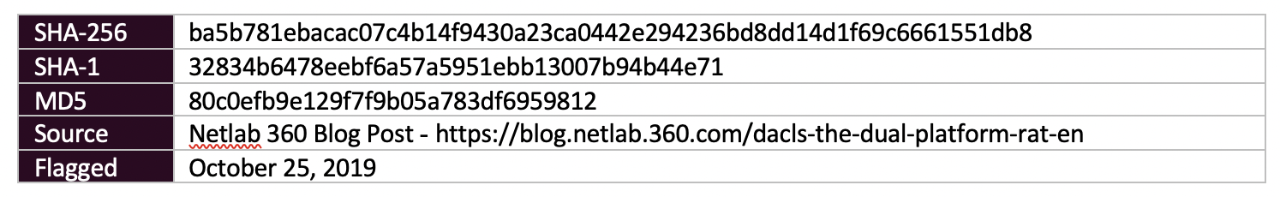 Figure 3 – Dacls RAT Sample
Figure 3 – Dacls RAT Sample
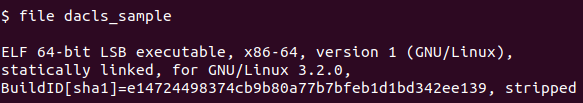 Figure 4 – File Command
Figure 4 – File Command
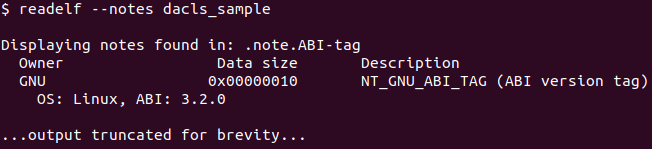 Figure 5 – Readelf --notes Command
Figure 5 – Readelf --notes Command
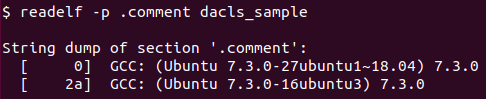 Figure 6 – "Readelf -p .comment” command displays the contents of ELF’s comment section
Figure 6 – "Readelf -p .comment” command displays the contents of ELF’s comment section
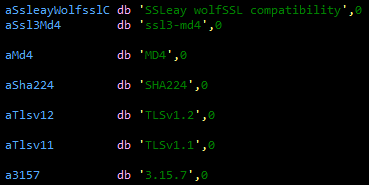 Figure 7 – Strings near wolfSSL String
Figure 7 – Strings near wolfSSL String
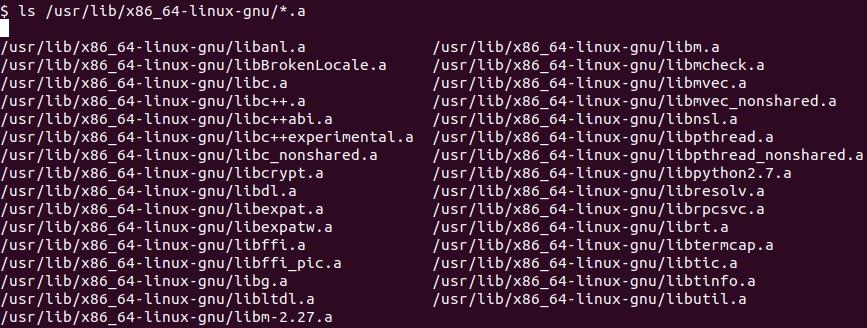 Figure 8 – Listing of /usr/lib/x86_64-linux-gnu/*.a
Figure 8 – Listing of /usr/lib/x86_64-linux-gnu/*.a
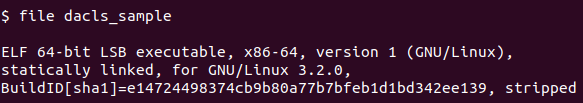
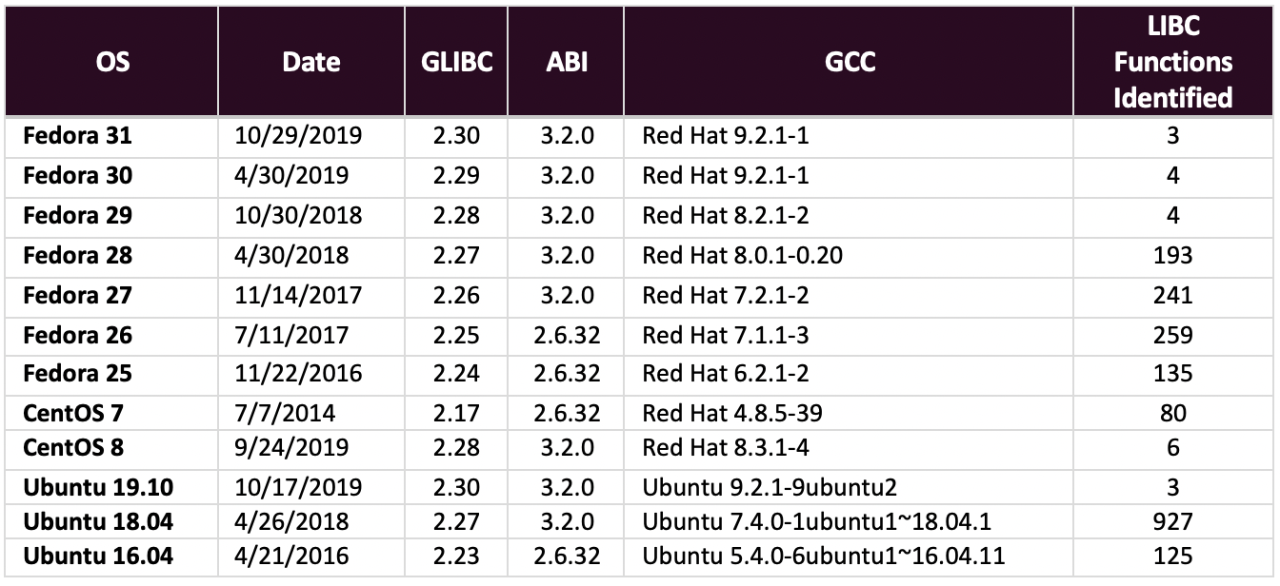 Figure 9 – Linux LIBC Signature Accuracy
Figure 9 – Linux LIBC Signature Accuracy